Everything you want to know about Phishing attacks.
(If you are interested in reading only about how to protect yourself from phishing, then go part IV of this article where it is mentioned "How to protect yourself from phising." It also includes some tips for Myspace users. And, Part V of this article has links to freeware utilities to protect yourself.)
This article is divided into four parts:-
PART IV HOW TO PROTECT YOURSELF FROM PHISING.
PART V FREE UTILTIES TO KEEP YOURSELF SECURED.

Well to start with for those who are not very familiar with the term, phishing is a criminal activity to fraudulently acquire sensitive information, such as passwords and credit card details, by masquerading as a trustworthy person or business in an electronic communication. Phishing is typically carried out using email or an instant message, although phone contact has been used as well.
Phishing involves sending email messages that seem to come from trustworthy sources, such as banking entities, but attempt to harvest confidential user data. In order to do so, they usually include a link that, if accessed, takes the user to a fake website. By doing this, users believe they are interacting with a trustworthy website, enter the information requested, which finally ends up in the hands of the fraudster.
Some of the most common characteristics that these forged email messages present are:
In addition to obscuring the fraudulent URL in an apparently legitimate email message, this kind of malware also uses other more sophisticated techniques:
RECENT SURVEY
Accorindg to Zdnet the study, released on Monday, showed that the number of brands under attack from phishing was up 20 percent from June and 12 percent from the previous record in May. According to the study "In a year, the number of brands has more than doubled, illustrating that online criminals are simply not settling for the large, popular organizations and financial institutions,"
Dan Hubbard, vice president of security research at Websense, said in a statement. "The increase in the complexity of attacks goes hand-in-hand with the massive growth in phishing Web sites and the targeted, broad selection of brands that has followed."
The U.S. topped the list of countries hosting phishing sites, with 29.9 percent, followed by the Republic of Korea with 13.3 percent, China with 12 percent, France with 5.9 percent and Australia with 4.6 percent.
Attacks are getting more sophisticated, the group found, noting that a malicious site is now capable of placing a Trojan horse onto a system without user interaction. The Trojan involved, Web Attacker, is a Russian do-it-yourself toolkit sold for anywhere from $20 to $300.
PART II MYSPACE USERS BE WARNED
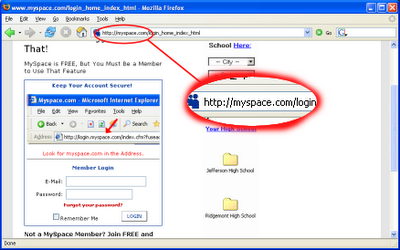
"Password-stealing MySpace log-in page removed"
Well that exactly was the heading of the Scmagazine article that appeared just two days ago.
Yes MySpace recently shut down a bogus profile page that was used to relay usernames and passwords to a remote server in France. The page was created using specially crafted HTML to eliminate the normal appearance of a user profile and instead resemble the real MySpace log-in page, according to internet monitoring firm Netcraft. Users would arrive at the page by following a phishing link. The fraudulent page was harvesting log-in details and communicating with a server in France, Paul Mutton, Netcraft's internet services developer, said Friday in a blog post.
With more than 100 million members and in the global top 10 of most visited websites, MySpace increasingly has become an attractive target for the malicious community, looking to take advantage of a young user set that is more trusting and less security minded than older generations.
Kevin Beecroft of Mashable labs in his very recent article says that MySpace Phishing Attack Appears on 3000 Pages. He goes on to say that a proportion of these pages are today active and will steal your email and password if you give it to them. The fake login pages are very convincing and even fooled Firefox into automatically filling in his credentials. Even cautious Internet users could get caught off guard by this trick.
You can also check out the netcraft page where you can see the illustrations on how the myspace login page was compromised.
I have given some tips for myspace.com users too to protect themselves under the "How to protect yourself from phishing" section.
PART III IMAGES OF SOME PHISHING SCAMS.
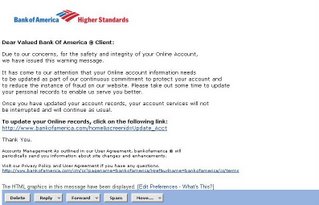
Above is a image from an email where Bank of America's name was used for the phishing attack. When the cursor was put on the hyperlink on which it says "To update your records click on the following link" it was clearly seen that link directs to a lycos.fr page and not Bank of America. That is why it is said always check for the url before u even login, whether it is yahoo account or bank account or whatever. And moreover banks will never ask you to fill in your personal data online.
Here is an example of phishing using paypal as the weapon.
Here is yet another example of how scare tactics are used to prompt the user to click on the link.
PART IV HOW TO PROTECT YOURSELF FROM PHISING.
Keep Antivirus Up To Date-
One of the most important things you can do to avoid phishing attacks is to keep your antivirus software up to date because most antivirus vendors have signatures that protect against some common technology exploits. This can prevent things such as a Trojan disguising your Web address bar or mimicking an https secure link. If your antivirus software is not up to date, you are usually more susceptible to attacks that can hijack your Web browser and put you at risk for phishing attacks.
Do Not Click On Hyperlinks In E-mails-
It is never a good idea to click on any hyperlink in an e-mail, especially from unknown sources. You never know where the link is going to really take you or whether it will trigger a malicious code. Some hyperlinks can take you to a fake HTML page that may try to scam you into typing sensitive information. If you really want to check out the link, manually retype it into a Web browser.
Take Advantage Of Anti-Spam Software-
Anti-spam software can help keep phishing attacks at a minimum. Many attacks come in the form of spam. By using anti-spam software, you can prevent most types of phishing attacks because the message will never end up in your mailbox.
Verify HTTPS (SSL)-
Whenever you are passing on sensitive information such as credit cards or bank information, make sure the address bar shows "https://" rather than just "http://" and that you have a secure lock icon at the bottom right hand corner of your Web browser. You can also double-click the lock to guarantee the third-party SSL certificate that provides the https service.
Many types of attacks are not encrypted but mimic an encrypted page. Always look to make sure the Web page is truly encrypted. The web address must begin with https:// and a little closed padlock must be displayed on the status bar of the browser.Double-click the padlock in order to view the digital certificate that confirms the website you are accessing is actually the one you expected.
Use Anti-Spyware Software-
Keep spyware down to a minimum by installing an active spyware solution and also scanning with a passive solution. If for some reason your browser is hijacked, anti-spyware software can often detect the problem and safely remove it.
Get Educated-
Educate yourself on how to prevent these types of attacks. A little research on the Internet may save you a great deal of pain if you are ever the victim of identity theft. You can report any suspicious activity to the FTC (in the U.S.). If you get spam that is phishing for information, forward it to spam@uce.gov. You can also file a phishing complaint at the "www.ftc.gov" (Federal Trade Commission). Another great resource is the FTC's identity theft page to learn how to minimize your risk of damage for ID theft. Visit the FTC's spam page to learn other ways to avoid e-mail scams and deal with deceptive spam.
Use The Microsoft Baseline Security Analyzer (MBSA)-
You can use the MBSA to make sure all of your patches are up to date. You can download this free tool from Microsoft's web site. By keeping your computer patched, you will protect your system against know exploits in Internet Explorer and Outlook (and Outlook Express) that can be used in phishing attacks.
Firewall-
Use a desktop (software) and network (hardware) firewall. On the desktop, you can use a software firewall or use Microsoft's built-in software firewall in Windows XP. The incorporation of a firewall can also prevent malicious code from entering your computer and hijacking your browser.
Use Backup System Images-
Keep a backup copy or image of all systems in case of foul play. You can then revert back to a pure system state if you suspect that a phishing attack, spyware, or malware has compromised the system.
Don't Enter Sensitive Or Financial Information Into Pop-up Windows-
A common phishing technique is to launch a bogus pop-up window when someone clicks on a link in a phishing e-mail message. This window may even be positioned directly over a window you trust. Even if the pop-up window looks official or claims to be secure, you should avoid entering sensitive information because there is no way to check the security certificate. Be sure to close pop-up windows by clicking on the X in the top-right corner. Clicking cancel may send you to another link or download malicious code.
Secure The Host File-
A hacker can compromise the hosts file on a desktop system and send a user to a fraudulent site. Configuring the host file to read-only may alleviate the problem, but complete protection will depend on having a good desktop firewall that protect against tampering by outside attackers and keep browsing safe.
Protect Against DNS Pharming Attacks-
This is a new type of phishing attack that doesn't spam you with e-mails but poisons your local DNS server to redirect your Web requests to a different Web site that looks similar to a company Web site (e.g. eBay or PayPal). For example, the user types in eBay's Web address but the poisoned DNS server redirects the user to a fraudulent site. This is what is considered new age phishing. This needs to be handled by an administrator who can use modern security techniques to lock down the company's DNS servers.
Always verify the information source -
Do not automatically reply to any email message that asks for your personal or financial information. If you feel uncertain about whether that company really needs the kind of information it is requesting, pick up the phone book and phone your usual contact, in order to check the information source.
Type the web address in your Internet browser yourself-
Instead of clicking on the links in the email message, type the web address (URL) in your browser, or use a previously defined bookmark. Even web addresses that look correct in the email message can be the path to a fraudulent website.
Reinforce your security-
Users making transactions through the Internet should install security suites that block this kind of threat on their computers, apply the latest security patches available through their usual vendors and make sure that they are operating in secure mode using digital certificates or communication protocols such as HTTPS.
Regularly check your accounts-
Monthly statements are particularly useful to detect irregular transfers and transactions, both operations that you did not make but are reflected in the statement and operations made online but not reflected in the statement.
Myspace users:-
With the recent phishing attacks on myspace.com it is always safe now that you log in through your own page. Don't go to someone else's page and then log in through that page when it says "You need to log in to do that" Instead always take the safer path of logging first directly through your own account.
And never use a password and email which you use for your financial or very personal reasons on myspace. Use a separate email account and a unique password only for myspace.
Also MySpace.com suggests on its site that users do not reply to email or pop-up messages that seek personal or financial information, or click on links found in such messages.
These tips should be followed not just for myspace but for other popular sites too. Combine these tips with all the other tips mentioned above and you will be safe.
PART V FREE UTILTIES TO KEEP YOURSELF SECURED:-

Go here to get some of the best free utilities to protect yourself. Check out the utilities under the "Essential Downloads" to get some of the best spyware/adware removal tools and anti-virus and internet privacy tools. I personally use some of these free stuffs simply because they are just too good even if they are free. Also Check out the most popular section and the Editor's pick section. There are some awesome free tools there. The best free utilities like the adware/spyware removable tool Spybot Search and Destroy, Zone Alarm firewall and AVG anti-virus are all there among all the other things you need to protect yourself. Take a good look there. Basis 5 things you need are:- An Antivirus, A firewall, An Antispyware (ideally two), Anti Trojan, And an Anti Rootkit.
Use the netcraft toolbar if you like to. Check it out here. It was netcraft tool bar user that detected one of the fake pages at myspace recently and reported it to netcraft.
Related Reading:-
27 steps to prevent Virus.
Best free Antivirus softwares.
Great free tool to detect spywares.
Keeping your password safe and related tools.
What are root kits and Rootkit detecting sofwares.
(This article was written based on information from the following sources and from my own experience)
Credits:-
Zdnet.
Whitecanyon.
Securityfocus.
Wikipedia.
Security.yahoo.
Kevin Beecroft of mashable labs.
Scmagazine.
Pandasoftware.
Netcraft.
This article is divided into four parts:-
PART I WHAT IS PHISING AND DETAILS ABOUT PHISHING.
PART II MYSPACE USERS BE WARNED.
PART III IMAGES OF SOME PHISHING SCAMS.PART IV HOW TO PROTECT YOURSELF FROM PHISING.
PART V FREE UTILTIES TO KEEP YOURSELF SECURED.
PART I WHAT IS PHISHING AND DETAILS ABOUT PHISHING:-

Well to start with for those who are not very familiar with the term, phishing is a criminal activity to fraudulently acquire sensitive information, such as passwords and credit card details, by masquerading as a trustworthy person or business in an electronic communication. Phishing is typically carried out using email or an instant message, although phone contact has been used as well.
Phishing involves sending email messages that seem to come from trustworthy sources, such as banking entities, but attempt to harvest confidential user data. In order to do so, they usually include a link that, if accessed, takes the user to a fake website. By doing this, users believe they are interacting with a trustworthy website, enter the information requested, which finally ends up in the hands of the fraudster.
Some of the most common characteristics that these forged email messages present are:
- Use of the names of existing companies. Instead of creating a company's website from scratch, fraudsters imitate the corporate image and website functionality of an existing company in order to further confuse recipients of the forged message.
- Use of the name of a real company employee as the sender of the spoofed message. By doing so, if recipients attempt to confirm the authenticity of the message by calling the company, they will be assured that the person that acts as spokesman of the company does actually work for the company.
- Web addresses that seem to be correct. Forged emails usually take users to websites that imitate the appearance of the company used as bait to harvest the information. In fact, both the contents and the web address (URL) are spoofed and simply imitate legitimate contents. What's more, legal information and other non-critical links could redirect trusting users to the real website.
- Fear factor. The window of opportunity open to fraudsters is very short, as once the company is informed that its clients are targets of these techniques, the server that hosts the fake website and harvests the stolen information is shut down within a few days. Therefore, it is essential for fraudsters to obtain an immediate response from users. On most occasions, the best strategy is to threaten them with either financial loss or loss of the account itself if the instructions outlined in the forged email are not followed, which usually refer to new security measures recommended by the company.
In addition to obscuring the fraudulent URL in an apparently legitimate email message, this kind of malware also uses other more sophisticated techniques:
- Man-in-the-middle. In this technique, the fraudster is located between the victim and the real website, acting as a proxy server. By doing so, he can listen to all communication between them. In order to be successful, fraudsters must be able to redirect victims to their own proxy, instead of to the real server. There are several methods, such as transparent proxies, DNS Cache Poisoning and URL obfuscation, among others.
- Exploitation of Cross-Site Scripting vulnerabilities in a website, which allow a secure banking web page to be simulated, without users detecting any anomalies, neither in the web address nor in the security certificate displayed in the web browser.
- Vulnerabilities in Internet Explorer, which by means of an exploit allow the web address that appears in the browser address bar to be spoofed. By doing so, while the web browser could be redirected to a fraudulent website, the address bar would display the trustworthy website URL. This technique also allows false pop-up windows to be opened when accessing legitimate websites.
- Some attacks also use exploits hosted in malicious websites, which exploit vulnerabilities in Internet Explorer or the client operating system in order to download keylogger type Trojans, which will steal confidential user information.
- Pharming is a much more sophisticated technique. It consists in modifying the contents of the DNS (Domain Name Server), either via the TCP/IP protocol settings or the lmhost file, which acts as a local cache of server names in order to redirect web browsers to forged websites instead of the legitimate ones, when the user attempts to access them. Furthermore, if the victim uses a proxy in order to remain anonymous while surfing the web, its DNS name resolution could also become affected, so that all the proxy users are redirected to the false server.
RECENT SURVEY
Accorindg to Zdnet the study, released on Monday, showed that the number of brands under attack from phishing was up 20 percent from June and 12 percent from the previous record in May. According to the study "In a year, the number of brands has more than doubled, illustrating that online criminals are simply not settling for the large, popular organizations and financial institutions,"
Dan Hubbard, vice president of security research at Websense, said in a statement. "The increase in the complexity of attacks goes hand-in-hand with the massive growth in phishing Web sites and the targeted, broad selection of brands that has followed."
The U.S. topped the list of countries hosting phishing sites, with 29.9 percent, followed by the Republic of Korea with 13.3 percent, China with 12 percent, France with 5.9 percent and Australia with 4.6 percent.
Attacks are getting more sophisticated, the group found, noting that a malicious site is now capable of placing a Trojan horse onto a system without user interaction. The Trojan involved, Web Attacker, is a Russian do-it-yourself toolkit sold for anywhere from $20 to $300.
PART II MYSPACE USERS BE WARNED

"Password-stealing MySpace log-in page removed"
Well that exactly was the heading of the Scmagazine article that appeared just two days ago.
Yes MySpace recently shut down a bogus profile page that was used to relay usernames and passwords to a remote server in France. The page was created using specially crafted HTML to eliminate the normal appearance of a user profile and instead resemble the real MySpace log-in page, according to internet monitoring firm Netcraft. Users would arrive at the page by following a phishing link. The fraudulent page was harvesting log-in details and communicating with a server in France, Paul Mutton, Netcraft's internet services developer, said Friday in a blog post.
With more than 100 million members and in the global top 10 of most visited websites, MySpace increasingly has become an attractive target for the malicious community, looking to take advantage of a young user set that is more trusting and less security minded than older generations.
Kevin Beecroft of Mashable labs in his very recent article says that MySpace Phishing Attack Appears on 3000 Pages. He goes on to say that a proportion of these pages are today active and will steal your email and password if you give it to them. The fake login pages are very convincing and even fooled Firefox into automatically filling in his credentials. Even cautious Internet users could get caught off guard by this trick.
You can also check out the netcraft page where you can see the illustrations on how the myspace login page was compromised.
I have given some tips for myspace.com users too to protect themselves under the "How to protect yourself from phishing" section.
PART III IMAGES OF SOME PHISHING SCAMS.

Above is a image from an email where Bank of America's name was used for the phishing attack. When the cursor was put on the hyperlink on which it says "To update your records click on the following link" it was clearly seen that link directs to a lycos.fr page and not Bank of America. That is why it is said always check for the url before u even login, whether it is yahoo account or bank account or whatever. And moreover banks will never ask you to fill in your personal data online.
Here is an example of phishing using paypal as the weapon.
Here is yet another example of how scare tactics are used to prompt the user to click on the link.
PART IV HOW TO PROTECT YOURSELF FROM PHISING.

Keep Antivirus Up To Date-
One of the most important things you can do to avoid phishing attacks is to keep your antivirus software up to date because most antivirus vendors have signatures that protect against some common technology exploits. This can prevent things such as a Trojan disguising your Web address bar or mimicking an https secure link. If your antivirus software is not up to date, you are usually more susceptible to attacks that can hijack your Web browser and put you at risk for phishing attacks.
Do Not Click On Hyperlinks In E-mails-
It is never a good idea to click on any hyperlink in an e-mail, especially from unknown sources. You never know where the link is going to really take you or whether it will trigger a malicious code. Some hyperlinks can take you to a fake HTML page that may try to scam you into typing sensitive information. If you really want to check out the link, manually retype it into a Web browser.
Take Advantage Of Anti-Spam Software-
Anti-spam software can help keep phishing attacks at a minimum. Many attacks come in the form of spam. By using anti-spam software, you can prevent most types of phishing attacks because the message will never end up in your mailbox.
Verify HTTPS (SSL)-
Whenever you are passing on sensitive information such as credit cards or bank information, make sure the address bar shows "https://" rather than just "http://" and that you have a secure lock icon at the bottom right hand corner of your Web browser. You can also double-click the lock to guarantee the third-party SSL certificate that provides the https service.
Many types of attacks are not encrypted but mimic an encrypted page. Always look to make sure the Web page is truly encrypted. The web address must begin with https:// and a little closed padlock must be displayed on the status bar of the browser.Double-click the padlock in order to view the digital certificate that confirms the website you are accessing is actually the one you expected.
Use Anti-Spyware Software-
Keep spyware down to a minimum by installing an active spyware solution and also scanning with a passive solution. If for some reason your browser is hijacked, anti-spyware software can often detect the problem and safely remove it.
Get Educated-
Educate yourself on how to prevent these types of attacks. A little research on the Internet may save you a great deal of pain if you are ever the victim of identity theft. You can report any suspicious activity to the FTC (in the U.S.). If you get spam that is phishing for information, forward it to spam@uce.gov. You can also file a phishing complaint at the "www.ftc.gov" (Federal Trade Commission). Another great resource is the FTC's identity theft page to learn how to minimize your risk of damage for ID theft. Visit the FTC's spam page to learn other ways to avoid e-mail scams and deal with deceptive spam.
Use The Microsoft Baseline Security Analyzer (MBSA)-
You can use the MBSA to make sure all of your patches are up to date. You can download this free tool from Microsoft's web site. By keeping your computer patched, you will protect your system against know exploits in Internet Explorer and Outlook (and Outlook Express) that can be used in phishing attacks.
Firewall-
Use a desktop (software) and network (hardware) firewall. On the desktop, you can use a software firewall or use Microsoft's built-in software firewall in Windows XP. The incorporation of a firewall can also prevent malicious code from entering your computer and hijacking your browser.
Use Backup System Images-
Keep a backup copy or image of all systems in case of foul play. You can then revert back to a pure system state if you suspect that a phishing attack, spyware, or malware has compromised the system.
Don't Enter Sensitive Or Financial Information Into Pop-up Windows-
A common phishing technique is to launch a bogus pop-up window when someone clicks on a link in a phishing e-mail message. This window may even be positioned directly over a window you trust. Even if the pop-up window looks official or claims to be secure, you should avoid entering sensitive information because there is no way to check the security certificate. Be sure to close pop-up windows by clicking on the X in the top-right corner. Clicking cancel may send you to another link or download malicious code.
Secure The Host File-
A hacker can compromise the hosts file on a desktop system and send a user to a fraudulent site. Configuring the host file to read-only may alleviate the problem, but complete protection will depend on having a good desktop firewall that protect against tampering by outside attackers and keep browsing safe.
Protect Against DNS Pharming Attacks-
This is a new type of phishing attack that doesn't spam you with e-mails but poisons your local DNS server to redirect your Web requests to a different Web site that looks similar to a company Web site (e.g. eBay or PayPal). For example, the user types in eBay's Web address but the poisoned DNS server redirects the user to a fraudulent site. This is what is considered new age phishing. This needs to be handled by an administrator who can use modern security techniques to lock down the company's DNS servers.
Always verify the information source -
Do not automatically reply to any email message that asks for your personal or financial information. If you feel uncertain about whether that company really needs the kind of information it is requesting, pick up the phone book and phone your usual contact, in order to check the information source.
Type the web address in your Internet browser yourself-
Instead of clicking on the links in the email message, type the web address (URL) in your browser, or use a previously defined bookmark. Even web addresses that look correct in the email message can be the path to a fraudulent website.
Reinforce your security-
Users making transactions through the Internet should install security suites that block this kind of threat on their computers, apply the latest security patches available through their usual vendors and make sure that they are operating in secure mode using digital certificates or communication protocols such as HTTPS.
Regularly check your accounts-
Monthly statements are particularly useful to detect irregular transfers and transactions, both operations that you did not make but are reflected in the statement and operations made online but not reflected in the statement.
Myspace users:-
With the recent phishing attacks on myspace.com it is always safe now that you log in through your own page. Don't go to someone else's page and then log in through that page when it says "You need to log in to do that" Instead always take the safer path of logging first directly through your own account.
And never use a password and email which you use for your financial or very personal reasons on myspace. Use a separate email account and a unique password only for myspace.
Also MySpace.com suggests on its site that users do not reply to email or pop-up messages that seek personal or financial information, or click on links found in such messages.
These tips should be followed not just for myspace but for other popular sites too. Combine these tips with all the other tips mentioned above and you will be safe.
PART V FREE UTILTIES TO KEEP YOURSELF SECURED:-

Go here to get some of the best free utilities to protect yourself. Check out the utilities under the "Essential Downloads" to get some of the best spyware/adware removal tools and anti-virus and internet privacy tools. I personally use some of these free stuffs simply because they are just too good even if they are free. Also Check out the most popular section and the Editor's pick section. There are some awesome free tools there. The best free utilities like the adware/spyware removable tool Spybot Search and Destroy, Zone Alarm firewall and AVG anti-virus are all there among all the other things you need to protect yourself. Take a good look there. Basis 5 things you need are:- An Antivirus, A firewall, An Antispyware (ideally two), Anti Trojan, And an Anti Rootkit.
Use the netcraft toolbar if you like to. Check it out here. It was netcraft tool bar user that detected one of the fake pages at myspace recently and reported it to netcraft.
Related Reading:-
27 steps to prevent Virus.
Best free Antivirus softwares.
Great free tool to detect spywares.
Keeping your password safe and related tools.
What are root kits and Rootkit detecting sofwares.
(This article was written based on information from the following sources and from my own experience)
Credits:-
Zdnet.
Whitecanyon.
Securityfocus.
Wikipedia.
Security.yahoo.
Kevin Beecroft of mashable labs.
Scmagazine.
Pandasoftware.
Netcraft.

0 comments:
Post a Comment