Test your firewall, browser and your internet or site speed.
You will find three sections in this article:-
SECTION I INTERNET CONNECTION OR WEBSITE SPEED TESTS.
SECTION II FIREWALL TEST.
SECTION II BROWSER TEST.
SECTION II FIREWALL TEST.
SECTION II BROWSER TEST.
____________________________________________________________________________________
SECTION I INTERNET CONNECTION OR WEBSITE SPEED TESTS.
____________________________________________________________________________________Well there are other sites that lets you check your Internet connection speed but I personally prefer these two sites because they are very easy to use and they each use different methods so that you can use both of these sites to have your connection speed tested in two different ways. Read on.

Mcafee speedometer.
What the Mcafee speed test does is that it sends a 150KB file to your computer and records the amount of time it took for your computer to receive it. Click on the "test your speed" link in the page and after a while the speedometer needle shows your speed and you can also see your speed on the digital counter below the needle.

Numion Internet speed tester.
Go to the page and scroll down and hit on the start button. check on the box against your country and language (usually by default it will be checked appropriately) before you do that.
What is different and I like about this test is that it simulates normal surfing behaviour by fetching small images (logo's) from the websites, and is heavily influenced by distance and latency. The average of all the micro-measurements is a very good (quantitative) representation of the (subjective) Internet speed as you experience it.
The other two handy tools you can see in the numion site are:-
Sitespeed.
Sitespeed lets you measure the speed of your website. If you have a website this is a handy tool. It tells you the speed of your website and displays the results in 7 comprehensive graphs. And it also provides you with details about how long do your visitors have to wait, whether your web server is becoming slower, whether your pages too big and also whether your website is fast even for remote visitors.
Stopwatch.
This tool can be used to measure the time it takes to load a particular web page of your choice. This is very interesting especially if you have some personal pages like one on myspace. I checked my myspace page and it was cool to see that it takes 10 secs to load. With some of your heavy duty graphics and stuff on your myspace page it would be interesting to watch the seconds flow by.
The beauty is that all these are free. So just try it.
____________________________________________________________________________________
SECTION II FIREWALL TEST
____________________________________________________________________________________Go the GRC probe test page first.
Once you get to the page click on proceed. And when you get to the next page you will see the following options:-
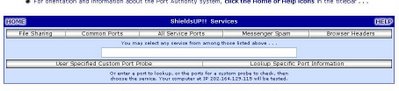
From the list you can choose which kind of scan you want to do. As you can see you have different options:-
1. File sharing:- If you want to check whether your personal computer is working as an Internet server without your knowledge nor your permission and that whether it is serving up all or many of your personal files for reading, writing, modification and even deletion by anyone, anywhere, on the Internet you should click on this option.
This will scan port 139 and also try to connect with NetBios to your pC and if the scan says that it cannot connect to either then it means your firewall is doing a good job.
2.Common parts:- This helps you to do a quick check up on the most common ports used for services like HTTP, HTTPS , RPC, NNTP etc:- If the scan gives you a stealth status that is best you can get. If any hacker doing a port scan looking for this ports to be open and your firewall has stealthed all these ports it simply means that the port scanner does not even know this ports exist on your Ip address. A good firewall always is in stealth mode.
3.All service ports:-Use this one if you want to probe all the service ports and not just the common ports. The scanner scans all these ports in a grid and if all the grids are in green then it means all these ports are stealthed. The scanner looks for open, closed and stealthed ports. If your firewall does not stealth the ports at least it should have closed the ports.
But stealth mode is what good firewalls are capable of doing so that any one using a port scanner with a malicious intent never even know such a port exists in your machine while the port scanning is on.
4.Messenger spam:-
You guys probably know the problem created by Microsoft's various servers that are open and running, by default, on port 135. So this test lets you verify that Windows Messenger spam can not reach the system you are currently using.
You will see the default message written on the space but if you want to write something else do that and then hit the "Spam me with this note" button. If your Internet service provider (ISP), personal computer system, personal firewall, NAT router, or network is not currently blocking UDP traffic into port 135, and if you are running a version of Windows with the Windows Messenger Internet server enabled and listening for incoming UDP messages on port 135, a number of "Messenger Service" pop-up dialog boxes will immediately appear on your system's screen.
5.User specified Custom port Probe:- If you want to probe only a particular port then you can type that port number into the space provided and then hit this button and it will only scan that particular port.
6. Look up specific port information:- Hitting this button does not probe any ports. This button can used if you want to know the information regarding a particular port. If you want to know what service a port stands for and what protocol it uses and things like that you can type the port number in the space and then hit the button to learn the information about that particular port.
Remember that a good firewall will always be in stealth mode.
If the firewall is good and in stealth mode then not a single packet will be received from your system while the GRC probe test is being done. Your system will ignore and refuse to reply to repeated Pings (ICMP Echo Requests). This means any hacker who uses the port scanner, does not even know that your machine even exists on the Internet. Some personal firewalls or security systems expose their users by attempting to "counter-probe the prober", thus revealing themselves. And that means the firewall lets your system to be advertised on the net which is not a good thing at all except for the person using the port scanner.
____________________________________________________________________________________
SECTION III BROWSER TEST
____________________________________________________________________________________The "Browser headers" button which you see among the other buttons (which you must have already seen in the screen shot of the GRC probe test page I have given above) can be used to find out what all information your browser is sending. Since it is not a firewall test and totally a browser test I have categorized it under this section.
Once you hit this button it will take you to a page which shows all the header information your browser is giving out to the world outside.
This page lets you to determine exactly what identifying information is being sent from your browser when it asks for any object from an Internet web server. If you choose to experiment with any of the third-party proxy and cookie filters, this page allows you to easily perform configuration experiments and to quickly verify that filtering is present and functioning as you expect and intend.
Once you hit the browser header button and get to the page you will see a whole lot of information there. You can use the "Feed browser this cookie" button to learn exactly how they operate by filling-in a non-blank name and value pair and also the "switch page to non-secure" button if you want to just check more details and do some experiments.
As many of you know your browser provides a whole lot of information to sites you visit and also to the third parties. With javascript and active x and cookies enabled it provides a whole lot of information. Even the pages you last visited or the page you came from is all know if the referrer logging is on.
Unfortunately with a million websites popping up each day it is hard to keep track of which one is good and which one is malicious. An unsuspecting user can just follow a link and land up in a site that uses malicious scripts and snooping techniques. The only way to work around this is by disabling the java scripts and active x and cookies before you visit an unfamiliar website.
You might be also interested to read about the firewall leak testing tool.
Also to be on the safer side read the article I wrote about phishing attacks. As the saying goes....a stitch in time saves nine.
