Everthing about Trojans and Anti Trojans.
Well, everyone has heard of Trojan horses, the ones in the greek mythology as well as the ones that affect our PCs. But there are still many who use the term Virus to describe trojans. But they should know that Viruses are totally in their own class than trojans and worms. They are all malwares though.
So viruses, trojans and worms are different from each other. A virus is a malicious code or a software program that attaches itself with a file or a program and spreads leaving infections as it travels. It is mainly created with the intention to destroy or damage a machine and the datas unlike spywares which are created mainly with the intention of making money through capturing the browsing habits of the user and is thus mostly a unhealthy marketing practice.
A worm is a software program and a single computer can send thousands of worms since worms can replicate itself in a single computer and sent itself out using the file or information transport features of your computer.An email worm can send itself to all the people inyour address book.A copy of the worm scans the network for another machine that has a specific security hole. It copies itself to the new machine using the security hole, and then starts replicating from there, as well.
As many of you might know Trojan horses are software programs that comes disguised as something else. A program claiming to be an excellent tool for repairing your hard disk would be actually a program that contains a trojan. Trojan horses does not replicate itself. But on the computer that it resides it can open up backdoors so that a malicious person can take control of your PC etc:- through that back door. SOme less harmful trojans can change your desktop, hijack your browser etc:-

Trojan horses are developing much faster than any other class of malicious codes.There are different types of trojans . Let us have a look at them:-
1.Backdoors: Alias: Hacker's remote access tool, Back door
Among the types of trojans this one is the most popular. A typical backdoor consists of two parts-client and server. The server is the one that is on the victim's machine and the client is the one the attacker uses to connect to the victim's machine. Some backdoors even have scanner utilities that allows the attacker to scan for machines installed with the server part. With the most advanced backdoors hackers can gain access to the machine and take full control including browsing through the victim's hard drive, receiving a screen shot and even use the webcam. But simple ones just allow upload and download and run files on the machine.
Most notorious backdoors: SubSeven, NetBus, Deep Throat, Back Orifice, Bionet, Master's Paradise.
2.Trojan downloader: Alias:Trojan Downloader, TROJAN-DWONLOADER, Win32.Trojan.Downloader, TrojanDownloader
This is a software program that connects to the internet on it's own and downloads program using the FTP or HTTP. This programs downloads the server part of backdoors that the attacker can use to connect to the victim's machine.
Notorious trojan downloaders are Aphex, Dlder, Small, WebDL.
3.Trojan-Spy and Trojan-PSW programs: This is classified into three categories:-
(a)Password stealing trojans: This can also be dropped by backdoors and some worms.It basically uses the keylogger to monitor the strokes and record it when the user has to to input login and passwords. This trojan can also send information about the victim's IP address etc:- to the hacker. The logged data is send over the net immediately or is submitted later. This type of trojans can install itself to the machine.
(b)Data stealing trojans: This looks for specific data or files on the victim's machine. They look for serial keys, or files where the user has stored his authentication informations etc:- And this is send over the Internet to the hacker. It can even send emails to the hacker in an excel file.
(c)Spy: This too can install on it's own and might be programmed in a such a way that it uninstalls itself after a certain period of time. The spy monitors the key strokes by using a key logger and also can spy on other activities on the victim's machine. And then this can sent this datas at certain intervals.
Well known Trojan-spy or Trojan PSW programs are Coced, Hooker, GOP, Kuang, Platan, Klogger.
4.Trojan Clickers: This kind of trojans hijacks the browser and re-directs it to specific urls. This can be used for the purpose of getting more traffic to a website and thus get more page impressions or hits and get revenue from ads or to mount a dos attack on a specific website or to lead the victim to a page where it has viruses, worms or trojans.
Trojan-Clicker.Win32.Agent.bm has been one of the trojans that has been making rounds in this category that disguises itself as the Microsoft Windows - Security Alert'. Once the user clicks on the "process with select of protection software button" it will redirect to a webpage that contains adwares. This trojan is also known as StartPage-EP , Troj/CWSC, TrojanClicker:Win32/Agent.BM , TR/StartPage.QC.2 , Trj/StartPage.HZ among the various AntiVirus makers.
5.Trojan Droppers: These are the ones used to install other trojans or other malwares onto the victim's machine. So, even if the victim does not install a malicious program on his own this one can install the other malwares on the machine.
6.Trojan Proxies: This one resides on the victim's machine and the hacker or a spammer can use this to re-direct their activities through the affected machine which would serve as a proxy. Thus a spammer or a hacker can have anonymous access to the Internet through the victim's PC.
7.Hearse: This is a new class of Trojans that is a combination of rootkits + trojans making it even more hard to detect the trojans. One of the trojans in this class is the Trojan-Spy.Win32.Bancos.pw which intercepts https traffic and was targetting two German banks. This kind of trojans can thus make the encrypted https traffic between the banks and the users insecure.

One of the most notorious trojans that has been used to blackmail the users is the Trojan.Win32.Krotten. The author of this one actually used 13 different versions to make it hard to detect. Instead of modifying the user files this one modified the system registry so that this was hard to delete. Since this modified the system registry it was possible to bring the system back to the state it was prior to getting infected. But the Trojan that followed this which was Gpcode created more havoc since it did not allow any way the the system could be brought back to it's prior state. Daideneg, Schoolboys, Cryzip, MayArchive are the other trojans that have been commonly used for blackmailing the victims.
Two trojans have been detected that effects the J2ME. One is the redbrowser that sends SMS to pay numbers without the users knowledge and consent. This trojan is capabale of running on a vast number of handsets that supports Java. The second trojan also sends SMS but to a particular number (1717) which is charged. Games.gsmland.ru was found to be the site that uses this number. Read about it here.
Talking about Trojans one can't leave out the IRC Bots which have worm spreading capability - like the ZOTOB worm, MYTOB worm, and lots more which are worm trojans. Worm trojans combines the lethal affects of the self replicating nature of the worm with the malicious effects of Trojans. Thus they not only infect a lot of machines quickly but mulitplies in one single machine. The machine becomes a zombie computer. This allows the hacker or the attacker to sell the BOTNET (group of compromised computers) to the highest bidder. These are then used for Distributed denial of service (DDOS) attacks, spamming, massive browser hijacking etc:-
Trojans have been delivered via spam with attachments containing malicious code, or downloaded using a vulnerability exploit. It should be noted that malicious users are currently showing a preference for mass spamming over the use of exploits. Also some viruses and worms are known to drop server parts on the machine. Another way of getting to install programs with trojans is by installing programs that claims to be something else and thus coaxing the user into downloading and installing it on the machine.
Since trojans are in a different class from Viruses all AntiViruses does not detect all trojans. That is why it is advised to use Anti-trojan softwares along with AntiVirus softwares. Some of the best Antivirus softwares like Kaspersky, Bitdefender, Mcafee, Norton, Trend Micro, F-secure etc:- are good at detecting most of the trojans out there. But since trojans evolve a lot and the codes are modified more often it is always good to have an anti-trojan software along with your ANtiVirus tool.
Also since more and more trojans are appearing in the form of rootkits it is also good to have a Anti-Rootkit software too. Spywares are also a variation of trojans and so add to the tally an Anti-spyware since they too are in it's own class and thus you need a specialised tool for that. And ofcourse you need a firewall to monitor the ports and to see if any unwanted programs are accessing the net or whether your ports are being scanned too much. Appropriate links are provided under "related reading".
Let us have a look at some of the tools that specialise in negating Trojans:-
Trojan Hunter 4.6 - Paid ($49) (Free to try for 30 days) Download here.
This is a paid software and among the Anti-trojan softwares out there this one is the best. This is free to try for 30 days but unfortunately the trial version does not allow online updates. The scanning is very fast. The paid version has live update and a good heuristics(heuristics means instead of looking just for known signatures it analyses the behaviour of a file and get rids of the suspicious files. Thus any unknown trojans or malicious codes that shows malicious behaviour is taken care of. Among the softwares in the Anti-trojan category this is the best. And unlike some of the products available it is good at detecting polymorphic trojans. Polymorphic trojans are the ones that change their characterestics to avoid detection. The only bad side to this kind of detection is that sometimes it can give false alarms.
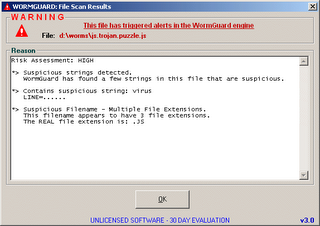
Wormguard 3 -PAID ($30) (Free to try for 30 days) Download here.
TDS 3 was one of the best Anti-trojans out there until the software maker discontinued it since they wanted to spend more time and resources on developing new products. Worm guard which is made by the same guys has been available since some time and the new improved version uses new deep-scanning generic detection technology and instead of depending on a data base to scan it thrives on having better heuristics and thus any trojans or worms that are new are identified and eliminated. This looks at the behaviour rather than the known signatures. Hence anything that has the characterestics linked to a trojan or a worm is spotted even if it is a new arrival which a software with poor heuristics that depends on a database might not spot until the database is updated.
But remember that a program that depends more on heuristics can trigger a lot of false alarms. A good program is the one that combines great database with great heuristics. And so you can expect some false alarms from this product. But use it to scan your PC and if you get an alarm scan the files with your updated anti-virus. This one does not use much resouces. And even whenever it gives an alarm it lets you have an idea of the file and which aspect of the file could be infected instead of just saying it is a virus. And even though this is not an out and out trojan hunter I have put this here since more and more trojans are taking up the Worm characterestics. Currently windows xp users and some other users are facing some compatibility issues (basically NIS issues) with this product. Version 4 will be available soon. So it might be better to wait until then.

AVG Anti-spyware (Formerly Ewido) –Free Download here.
Even though this is classified as Anti Spyware this works as a good Anti-trojan. The problem is that when it comes to the Anti-Trojan category not many free good free softwares are available. Ewido has always been concentrating on malwares especially in the class of trojans. And there is only a thin line between a spyware and a trojan. A spyware supposedly is installed on the PC with the "informed consent" of the user where as trojans trick users into installing the software. Carrying on with Ewido's tradition of being more of an Anti Malware software that concentrates on trojans and spywares the AVG anti-spyware does a good job for a free software. There is a paid version available of this product. The difference between the paid software and the free version is that there is no real time protection in the free version and no kernel level protection. However the on demand scanning is a good one. This product is also good at detecting polymorphic trojans.
Note: This works only with windows 2000 and above version. Among the free version this is the best.
a-squared - FREE Download here.
This is also a good Anti-trojan in the free category. This is actually the free version of Emsisoft's Anti-malware. The free version does not have real time protection, auto update and scheduled scan. But the data base is not compromised and you can manually update. However one should keep in mind that it is not a highly rated software. But again not much choices available in the free category when it comes to ANti-trojans. The scanning is not that fast either. use it in combination with another spyware and anti-trojan.
Like I mentioned earlier one should have a software that specialises in each category viz:- A firewall, an Anti-trojan (Ideally two), an AntiVIrus, an ANti Rootkit and a anti-spyware (Ideally two)
You can also find info on Anti-spywares and the HijackThis tool for advanced users here.
Related Reading:
Mobile phone malwares, blue tooth hacking and protection.
What are rootkits and related softwares
27steps to prevent virus
Free antivirus softwares
Zone Alarm firewall.

0 comments:
Post a Comment